One critical aspect of the information and communications technologies of the smart distribution network is cyber-security, which includes physical and system security.
Cyber-security covers the protection of networks and servers from unauthorized accesses and malicious attacks. It also covers the protection against compromised control and measurement units that can harm the system, physical security, secure state estimation, intrusion detection, etc.
Based on experiences gained from developed IT and telecommunication systems, it can be anticipated that the grid will be a potential target for malicious, well-equipped and well-motivated adversaries.
An attack may use up the systems’ own resources. These attacks can jeopardize the normal operation of the power distribution system and sometimes can be highly dangerous.
Furthermore, threats such as fiddling with financial information may cause a major economical disturbance, if they are not monitored carefully.
At the consumer end, unprotected energy-related data can invade the privacy of consumers. In particular, communications signals in AMI may disclose information about where people were, when and what they were doing.
Although contemporary security technologies, such as virtual private networks (VPNs), intrusion detection systems (IDSs), public key infrastructure (PKI), anti-virus software, firewalls, etc., have well protected the IT infrastructure, before deploying they need to be proven in systems that perform the critical operations and control of smart distribution networks.
Basic Cyber-Security Issues
Distribution network protection equipment and control and automation schemes use standardized data interchange and network implementations so as to make these applications interoperable among different vendors.
Accordingly, substations can now be interconnected with open networks such as corporate networks or the Internet, which use open protocols for communication.
When proprietary solutions were used, they brought obscurity (as the formats and protocols are proprietary, it can be very difficult to interpret and hack into them) and isolation (as the substation network is not connected to the outside world, it can’t be accessed from the outside world).
However, open protocols mean that the security provided by obscurity and isolation cannot be assumed. This leaves the networks vulnerable to cyber-attacks.
With the intention of avoiding such cyber-attacks, cyber-security measures are implemented. Cyber-security considers the following in its design:
- Confidentiality – preventing unauthorized access to information
- Integrity – preventing unauthorized modification
- Availability and authentication – preventing denial of service and assuring authorized access to information
- Non-repudiation – preventing denial of an action taking place
- Traceability and detection – monitoring and logging of activity to detect intrusion and analyze incidents
The threats to the system may be unintentional (e.g. natural disasters, human error), or intentional (e.g. cyber-attacks by hackers).
Cybersecurity is attainable with a range of measures such as closing down vulnerability loopholes, assuring availability, implementing adequate security processes and procedures and providing appropriate technology such as firewalls.
Some common cyber-security vulnerability loopholes include:
- Indiscretions by personnel, e.g. users keeping passwords in locations visible to others
- Bypassing of controls, such as users turning off security measures to access the system
- Bad practice, such as users not changing default passwords, or everyone using the same password to access all substation equipment
- Inadequate technology, where the substation is not firewalled or the firewall is not tailored for substation protection
Solutions That Ensure Cyber-Security in Distribution Networks
Processes and procedures used in distribution network ICT infrastructure are required to assure a secure exchange of the following categories of information:
- Security context: This defines information that allows users to have access to devices. It includes passwords, permissions and user credentials.
- Log and event management: This includes security logs, which are stored in different IEDs.
- Settings: This includes information about the IED, such as the number of used and unused ports and performance statistics.
- Datagrams: Packets of information exchanged between IEDs.
The open system interconnection (OSI) 7-layer model for peer-to-peer communication enables security measures to be applied at the Transport layer (layer 4) and the Application layer (layer 7).
Transport layer
At the Transport layer, the dialog between two devices is controlled. The connections between the two devices in question are established, managed and terminated at this layer by using either the transport control protocol (TCP), which ensures end-to-end reliable delivery using three-way handshaking, or the user datagram protocol (UDP), which attempts best effort delivery.
Applying security to this layer is known as Transport Layer Security, and the most common protocol used here is the TLS protocol, which is also known as secure socket layer (SSL).
Security measures applied to the Transport layer guarantee confidentiality, integrity, and authenticity, but because they rely on security provided by the Transport layer, this type of secure data exchange is limited to point-to-point communication.
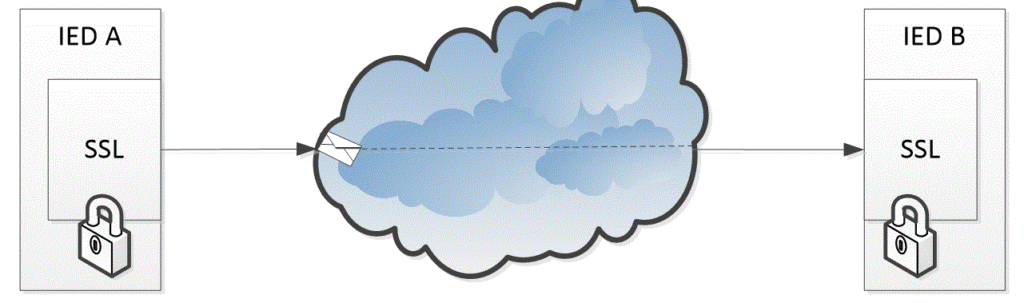
Figure 1 shows peer-to-peer communication between two IED nodes. The message from node A to node B is secured using the SSL protocol to prevent any possible access on its way through the network, represented by a cloud in the middle.
Figure 1 TLS secure communication.
Application Layer
A more flexible solution can be implemented by applying security at the Application layer, whereby messages themselves are secured independently of the Transport layer on which they are exchanged.
The application of security measures at the Application layer produces a service-oriented architecture (SOA).
SOA is based on web services that are message oriented. Secure messages can be sent between any of the devices in the network and are not limited to point-to-point communication.
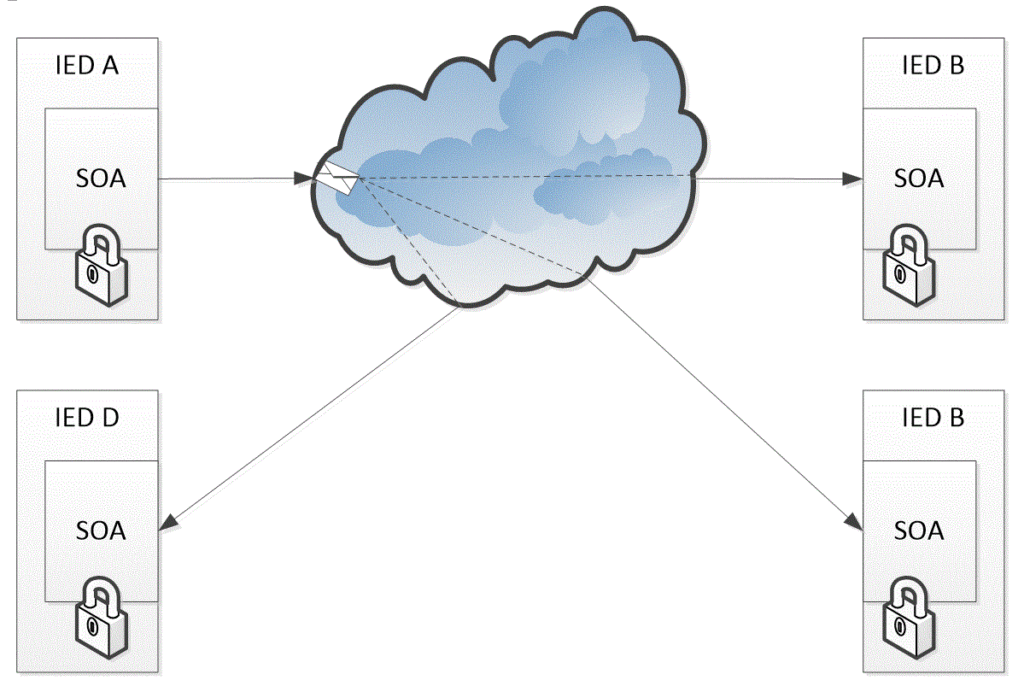
SOA solutions are not prescribed to any specific profile, but the device profile for web services (DPWS) protocol provides an appropriate level of security for substation automation. Its message transfer is shown in Figure 2.
In this case, the IED node A communicates with the IED nodes B, C and D using DPWS, which enables web profile interfacing. This is not restricted to peer-to-peer communication and enables communications among multiple nodes simultaneously and securely.
Figure 2 DPWS secure communication.
In addition to cyber-security on end-to-end message delivery, authentication, authorization (more about MFA authentication), and accounting (AAA) also have a significant role to play in granting access.
Role-based access control (RBAC) is a robust approach to control unintentional access by defining different classes of users granting different rights of access to different information in the devices on the network.
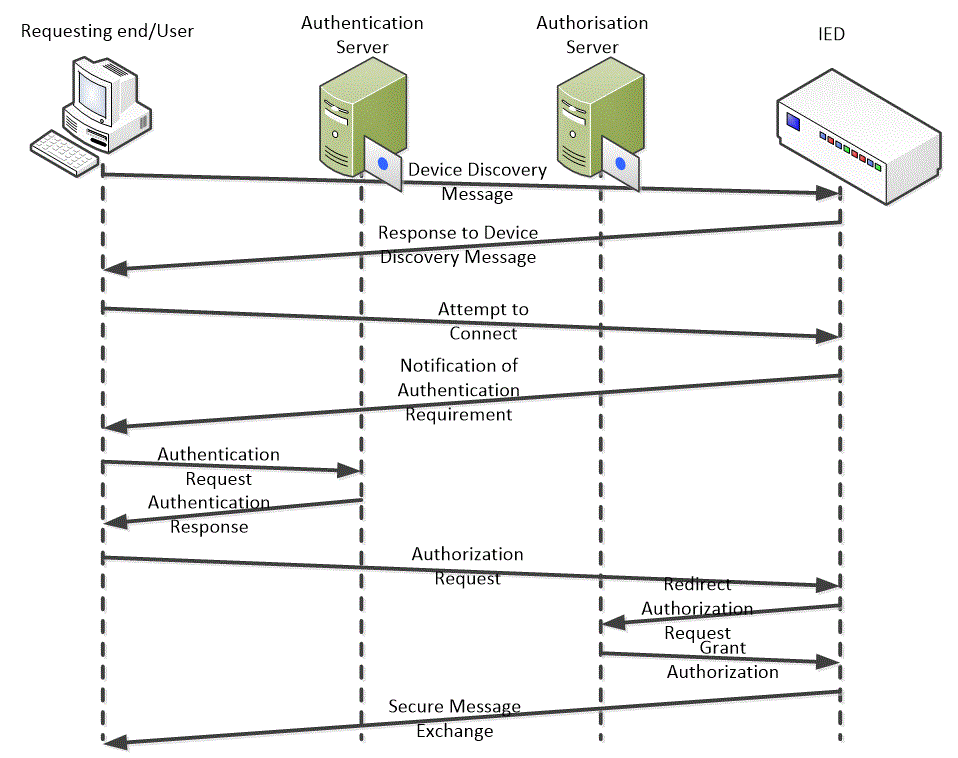
The following example illustrated using Figure 3, shows how an AAA server is used to implement RBAC.
When an IED or other networked device attached to the network is attempted access by a user through the network, an automatic device discovery process is performed. At the end of this step, the user selects the device to be connected with.
The selected device requests a token from the user to prove that he/she has been authenticated by the security server. The user transfers this token to the IED. The IED then requests the user roles and credentials from the authorization server.
If the roles and credentials are certified, a secure exchange of data can occur between the devices’ applications.
Figure 3 Implementing RBAC using an AAA server.