Cloud Computing Security Issues
Just as many companies and organizations are attentive and responsive to security concerns within their private networks, there are also security concerns when moving to a cloud environment.
One of the biggest security issues that cloud service providers must address is access. The question facing service providers is, “How can authorization be restricted to allow only authenticated and legitimate user access to the cloud?” From a business perspective, an organization is going to want assurances that security controls have been implemented and updated before they move sensitive information to the cloud.
Security control in the cloud is implemented by:
- Preventive controls – identify networking equipment that has design or programming flaws
- Detective controls – search and identify threats that can exploit design or programming flaws
- Corrective controls – search and identify which actions can counter or mitigate attacks
There are several items that concern business data and operations. If these sensitive items cannot be secured, then the value of cloud computing diminishes.
Business Security
Companies and organizations should be aware of a number of issues regarding data protection. This data can be internal (organizational) or external (customers/clients). Questions that need to be posed before migrating to the cloud are as follows:
- Where will our company data be stored in the cloud environment?
- Will our company data be stored within data stores accessed by other customers?
- In the event of a disaster at a cloud vendor site, will our data be accessible?
- How can the organization ensure that data will not be used by the cloud vendor and will remain confidential?
- How can our company ensure only authorized users have access to the data in the cloud?
- Will data integrity be maintained if the cloud vendor systems are hacked or if the vendor goes out of business or if the vendor is acquired in a business merger with another company?
- Will the cloud service provider have the tools in place to detect malicious behavior within their environment?
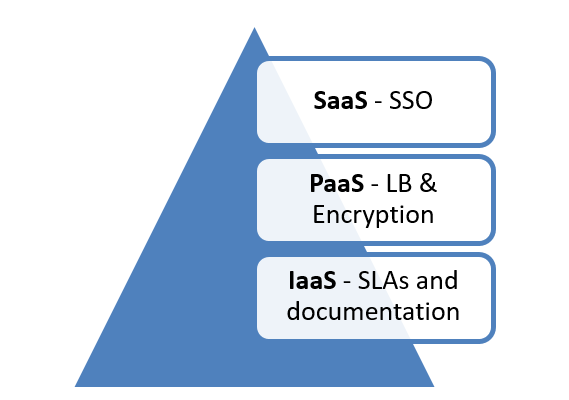
Companies and organizations must also consider security concerns based on the type of cloud service they acquire – see Figure 1.
Figure 1: Addressable Concerns per Cloud Type
SaaS providers can use single sign-on (SSO) to give users access to applications hosted in the cloud. For example, when a user logs into a Google account, they have access to Gmail, Google drive, and other applications, based on a single login.
PaaS providers can ensure platform availability by introducing load balancers (LBs) into the environment. Encryption is another feature implemented within the PaaS cloud to address security.
IaaS providers should define, in a service level agreement (SLA), who has access to the different parts of the cloud infrastructure. The SLA should also include network maps of the cloud environment and any links connecting to third-party cloud providers. Lastly, to avoid waste and unauthorized creation of virtual machines (VMs), a change management process should be included in the SLA.
Malicious Software
Due to the interconnected, homogenous computer systems seen in cloud DCs, the threat of malicious software, or malware, proliferating through the cloud environment is a concern. Some cloud providers have system architectures and platforms to mitigate this kind of risk.
- Malicious code can be copied from external devices and placed within the cloud environment. This was the case with the Stuxnet worm
- Cloud administrators within the provider facility can modify internal computer and network settings.
Cloud security introduces a complex set of issues for a business interested in migrating to a non-private cloud environment. Cloud service providers should be vetted to ensure security within the cloud is effectively implemented and updated on a regular basis.
Vendor Lock-In
Another area of concern for businesses and organizations who adopt a cloud solution is vendor lock-in. Vendor lock-in happens when a provider uses proprietary technology that cannot be easily transferred to another cloud provider. This can force a company to either incur a significant cost in recreating their environment (data and infrastructure) or be locked into using the same vendor, even if their technology is no longer sufficient to meet business needs. Vendor lock-in should be a major consideration in the selection of a cloud provider.
Cloud Levels of Maturity
Cloud computing can enhance business value at three different levels.
- The base level is the utility level. Here companies can benefit from the availability of flexible computing resources and pay-per-use models.
- The next intermediate level is the process-transformation level. This level introduces new business processes that are a result of improved capabilities delivered from cloud computing. An example of this level would be an incident ticketing system that has transformed from being at a specific (local) location, into a web-based ticketing system that is accessible around the globe so that issues can be identified and responded to more effectively.
- The last and most advanced level is the business-model-innovation level. This level is where not just the incident ticketing system, but the accounting, sales, support, and many other business systems utilize cloud computing. Another real-life example is when non-competing companies partner together to find ways to increase the competitive advantage in their industries (e.g., Amazon and Microsoft – Kindle on the PC).
These three levels of advancement, or maturity, build upon each other to give businesses a potential advantage, and they help guide organizations to identify future value in a product offering (e.g., service, process, etc.).
Time to Market
Cloud computing increases the resources available to organizations, which enable them to test and deploy applications faster, and in turn making it possible for them to enter the market sooner. Compare a company that has to purchase needed IT equipment and has to order additional resources once it has been determined that the project is larger than expected. The time required to acquire these IT resources reduces the ability of the company to release a product or service on time. However, if this same company used cloud services, they would have the ability to scale up and provision new equipment more easily, reducing the time to market (TTM).
Security controls are implemented to mitigate security concerns such as malware, availability, and accessibility. Vendor lock-in is also a major concern that organizations must face when moving into the cloud; a service interruption because a cloud service provider is using some proprietary technology, hardware or software, can have far-reaching effects on customers; a user can be tied in to a proprietary service and not be able to move to another cloud service provider.
One should be keenly aware of the pros and cons of a migration to cloud computing when deciding whether or not to adopt such a solution.
- You May Also Read: How Cloud Technology Enables New Business Models