Before we get too far ahead of ourselves, let us back up and establish some fundamentals. A fundamental aspect of cloud computing is that it involves a network, and more specifically, the Internet. If we were to examine our own connectivity to the Internet, we see that browsers are the network applications that make it possible. It does not matter if we use Internet Explorer, Firefox, Chrome, Safari, or another browser; the browser is our gateway to the Internet. Another term that can be applied to the browser is a client.
A client is a piece of software that allows us to access another piece of software being run on another computer.
Often, a computer running software that we want to access is called a server. What we have just described is a client-server network association. For us, the network between the client and the server is the Internet.
Table 1: Types of Clients
| Types of Client | Examples |
| Thick | Traditional browsers – Internet Explorer (IE), Firefox, Chrome, Safari… |
| Thin | Server provided client – Microsoft Terminal Services, X Windows, Citrix… |
| Mobile | clients – Safari, Chrome, Firefox, and IE… |
Application Program Interface (API)
It should be noted that the client and the server have a specific means of communication with each other. This methodology is commonly referred to as an application program interface (API). This API allows the client and server to establish a session, exchange information, and terminate the session. The API provides the framework and the rules necessary for these tasks to be accomplished.
Network Models
The easiest network model to visualize is two computers communicating with each other, connected together on the same physical network segment. This is a peer-to-peer network.
The obvious limitation is that only two computers are communicating. A third computer can be added to the network, to act as a server. The server has the obvious advantage in that it can share information with more than one client. For this reason, this networking model is called client-server networking.
Search for Extraterrestrial Intelligence (SETI) Project
With the introduction of the Internet, larger and larger networks were being built on the client-server architecture. When NASA canceled the SETI project, the SETI League was formed and it seized on the opportunity to encourage home/business computer users to allow SETI to use their idle computers to further their research. It did so by writing a software client so that individuals can install the client on their computers. The client allows SETI to off-load analysis tasks onto these systems to help further the SETI study. This was born grid computing. While the concept of grid computing is simple, the use of computing utilities is not. Grid computing is elastic in the sense that computers are added and deleted dynamically, whereas utility computing is a fixed environment of computer resources. Computer utilities allow smaller businesses, those who could not afford the expense of mainframe computers, to buy time and resources to handle their computing needs. Leaders in utility computing include Electronic Data Systems (EDS), Perot Systems, Affiliated Computer Systems (ACS), and Control Data Corporation (CSC).
This brings us full circle with virtualization and cloud computing. Review the approaches to system development below.
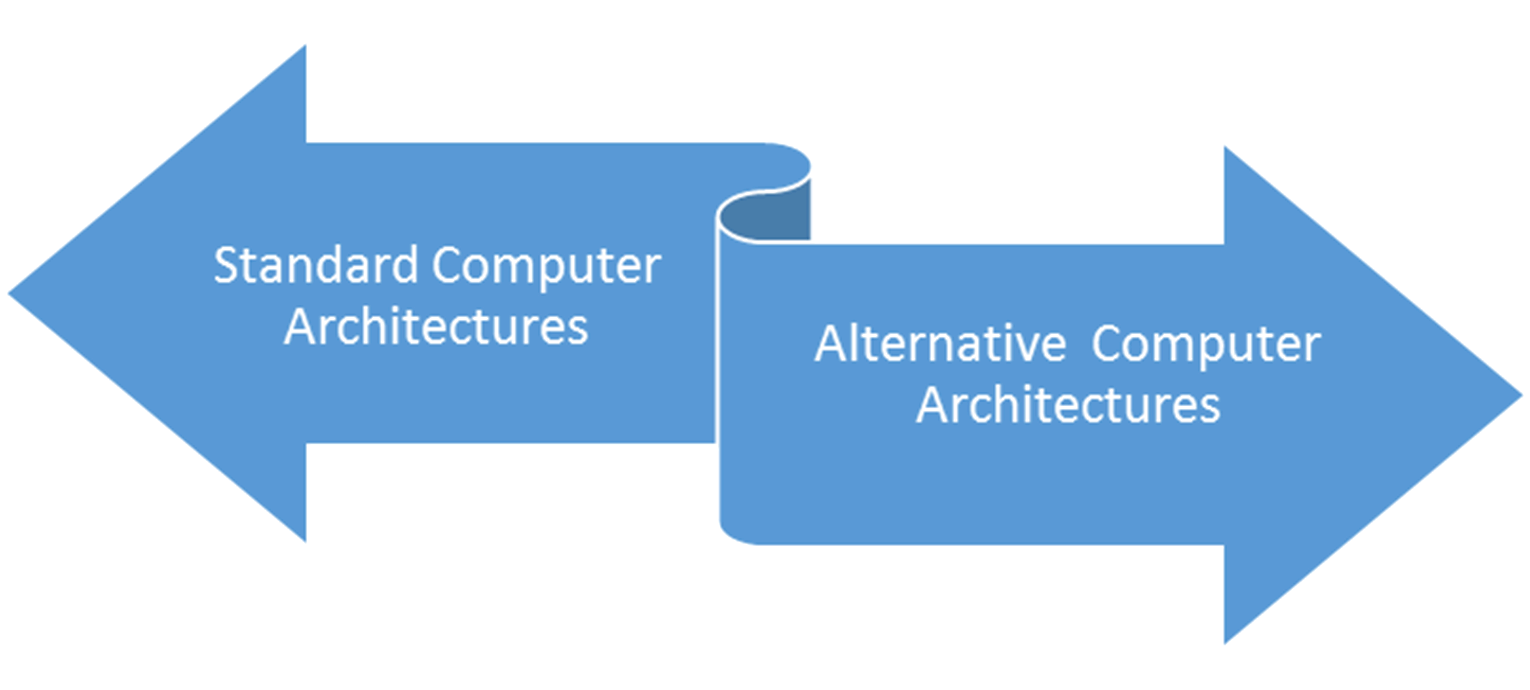
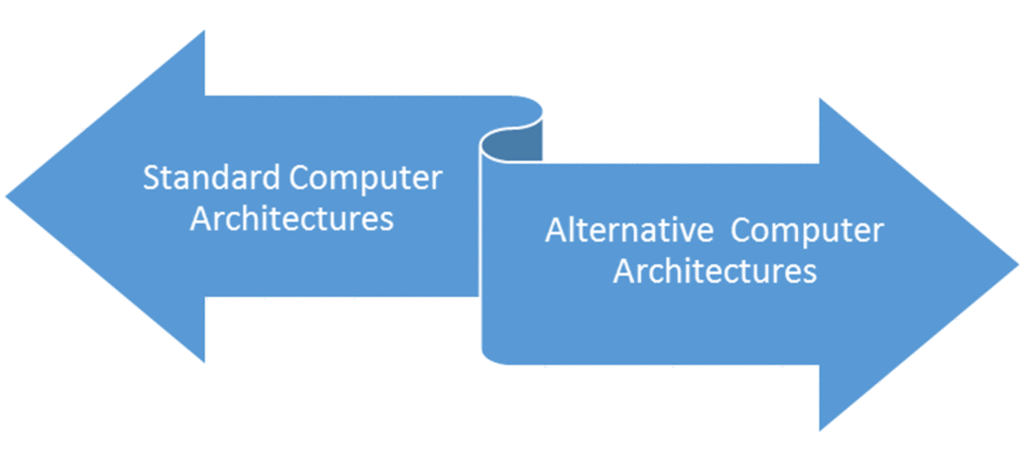
Standard Computer Architectures: The standard notion is that each computer system requires its own physical assets.
Alternative Computing Architectures: The alternative to the standard notion, is that a single computer system/architecture (with physical assets) can be used to create several virtualized computer systems.
Figure 1 contrasts standard computing and the alternative of computing with virtualization. Cloud computing is the business of virtual computing and fast provisioning of computer resources on the pay-per-use model. The figure shows the diverging architecture of standard and alternative computing architectures.
Fig.1: Approaches to System Deployment